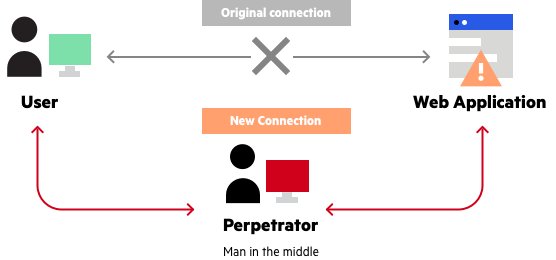
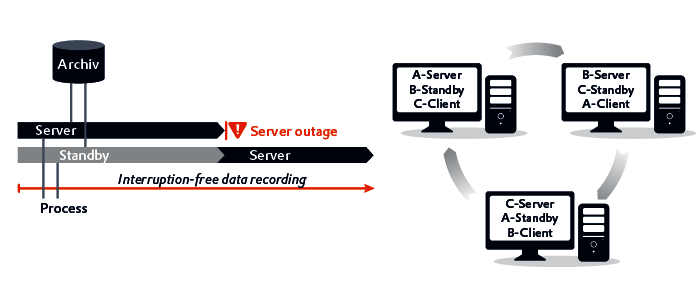
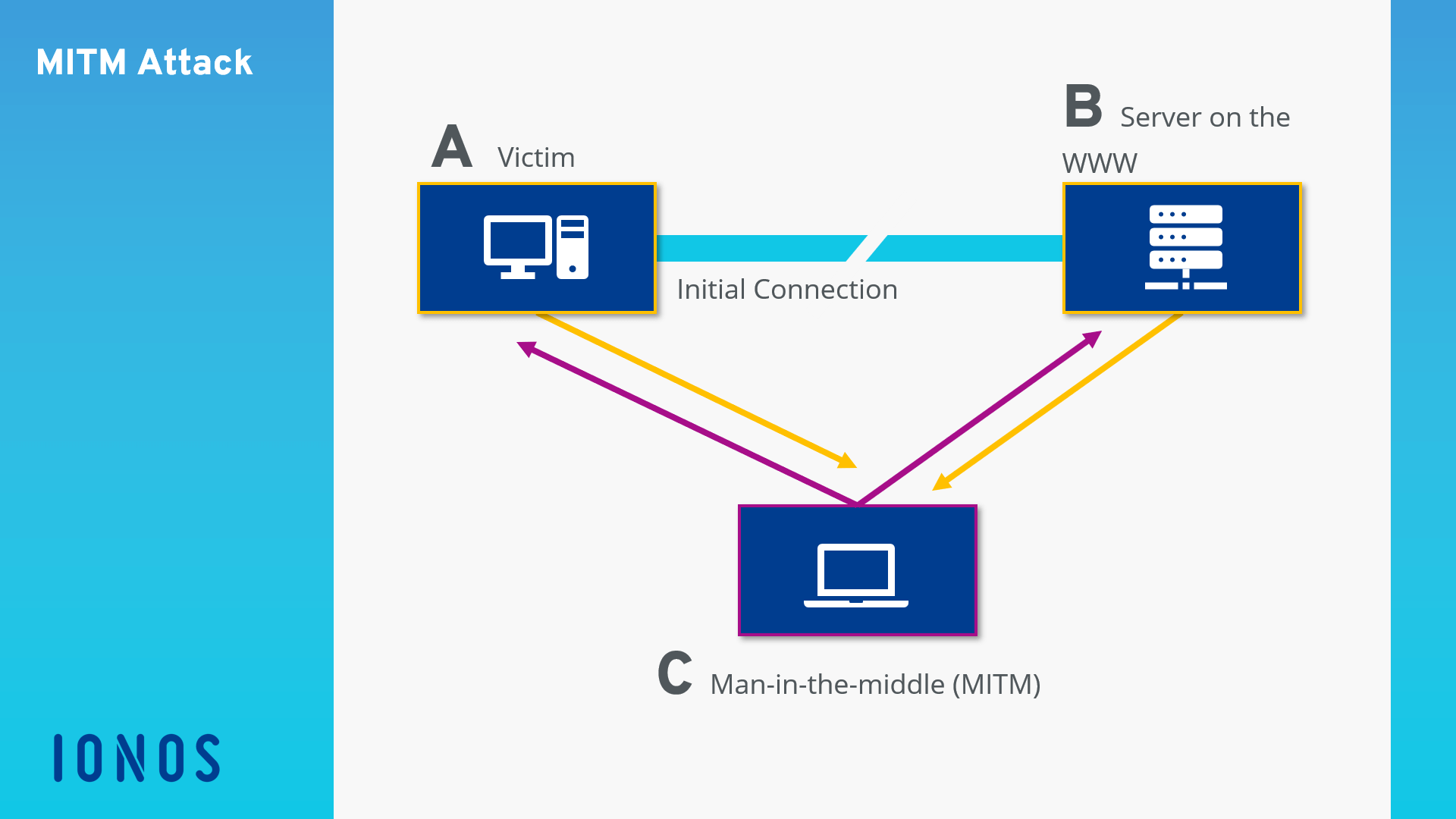
Mobile Critters: Part 1. Man In The Middle Attack. by Kaymera - secure calls & encrypted messages for you and your team

Protocol-level attacks: (a) Man-in-the-middle attack, (b) Brute forcing... | Download Scientific Diagram
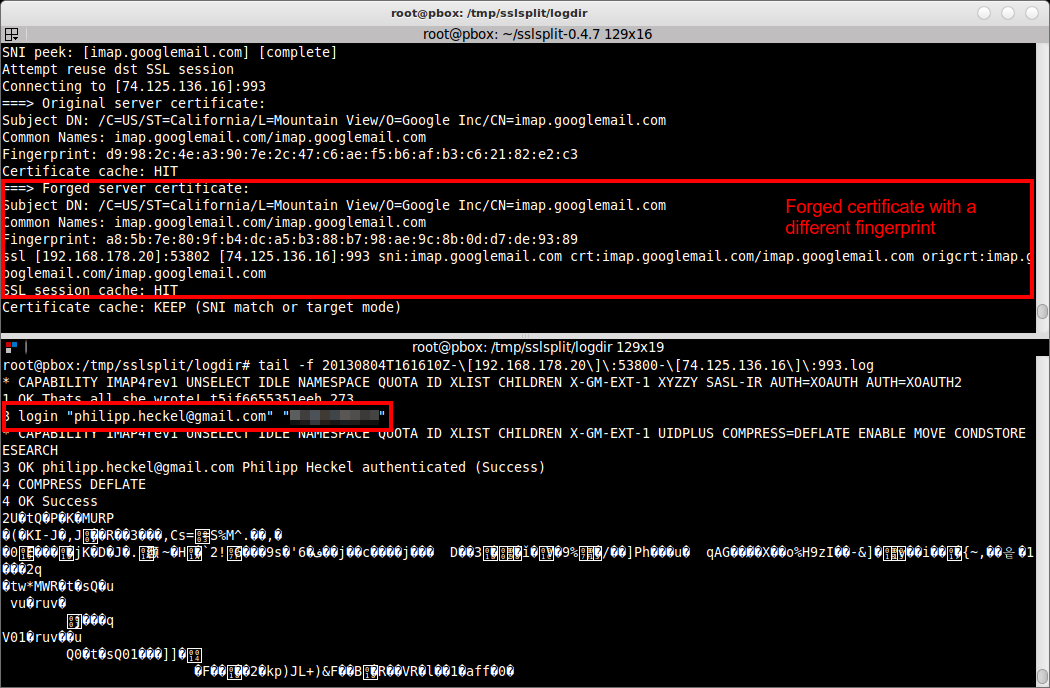
Use SSLsplit to transparently sniff TLS/SSL connections - including non-HTTP(S) protocols - Philipp's Tech Blog
![C] CSAPP Proxy Lab C] CSAPP Proxy Lab](https://images.velog.io/images/binsu/post/a8162ad4-78fe-4238-bd73-ac924121c376/image.png)